SOPS
In this guide, we will walk you through automating your Kubernetes Secrets encryption with Runme to ensure your encryption and decryption processes are automated and properly documented to improve your secret management.
Prerequisites
To get started, ensure you have the following:
- Clone the Repository: We have created a notebook repository containing all the instructions and commands required for this guide. Ensure to clone the repository.
git clone https://github.com/stateful/blog-examples.git
cd kubernetes/k8s-secret/sops
- Install Runme: Install the Runme extension on VS Code and set Runme as your default Markdown viewer.
This guide will focus on using the Mac specifications. If you use a Linux OS, follow the instructions in the Linux Markdown files.
Securing Secrets with SOPS
To encrypt your Kubernetes secrets using SOPS, you need an advanced security measure, access to a cloud provider, and a Key Management Service (KMS). For this guide, we will use an AWS KMS key.
Navigate to the SOPS file in the repository you cloned earlier and open the Markdown file based on the specifications of your operating system to follow up on this section of the guide.
Installation of SOPS
Run the command within your Runme cell to install kind, kubectl, sops, and awscli
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
brew install kind
brew install kubectl
brew install awscli
aws --version
aws configure
Here is a pictorial representation of the command in Runme and the corresponding output when it is successfully executed.
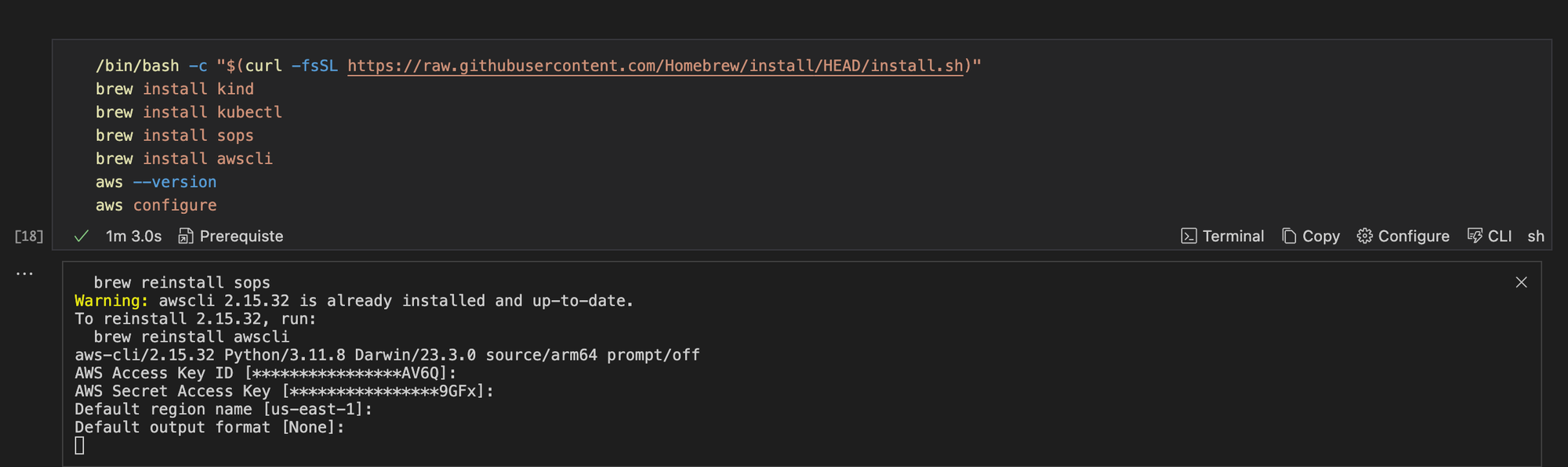
Finally, configure the installed AWS CLI in your Runme Terminal.
installation of SOPS
brew install sops
Create a KMS Key within your Runme Cell
You need a KMS key to encrypt and decrypt your secrets. As mentioned, we will use the AWS KMS key to carry out this action.
Create a cell for this section and run the command below in your Runme cell:
export alias
aws kms create-key --description "key-runme" | jq -r '.KeyMetadata.KeyId'
keyid=$(aws kms create-key --description "key-runme" | jq -r '.KeyMetadata.KeyId')
aws kms create-alias --alias-name "alias/$alias" --target-key-id $keyid
This command will prompt you to input a value for alias and create a KMS key. It will filter the output only to show the key ID and turn it into an environment variable called keyid. Once you run this command, you will get an output similar to the one in the image below.
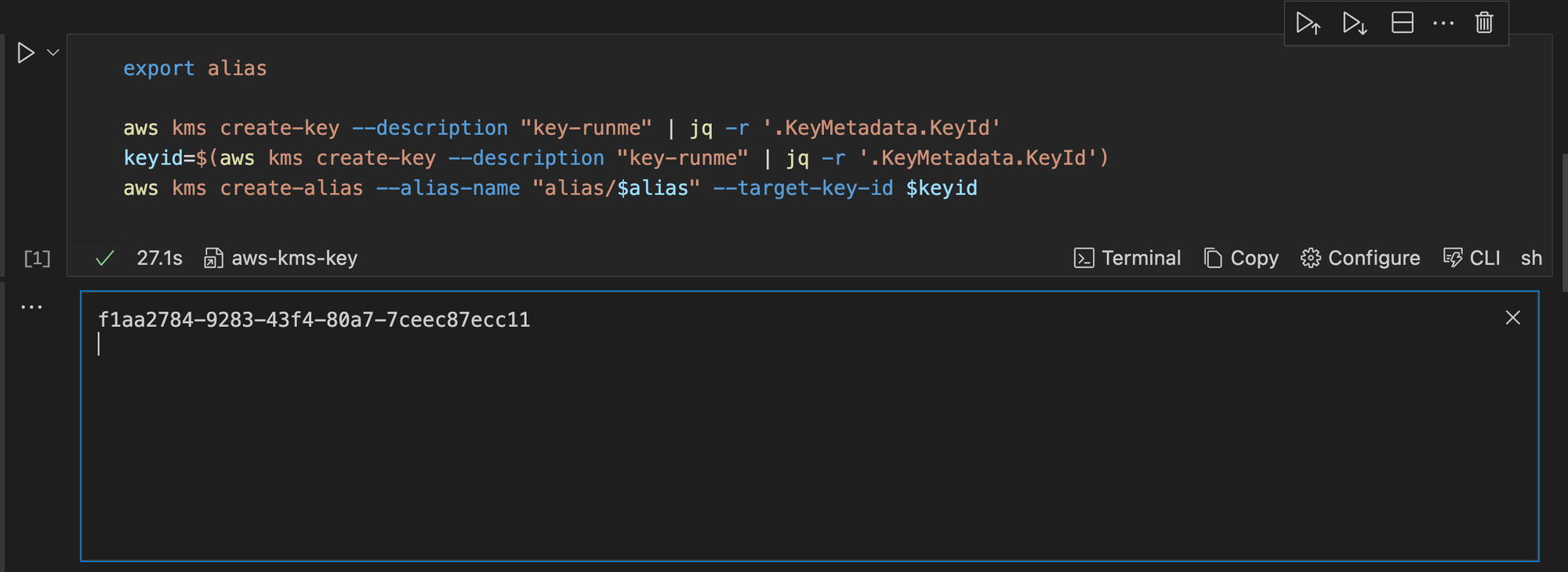
You can also save this output to the Runme cloud for future use with the Runme auto-save feature.
Configure SOPS in Runme
To configure your SOPS, specify how to encrypt your secrets, then define the encryption keys. To do this, run the command below in your Runme cell.
export region
export accountid
export alias
echo "creation_rules:
- kms: arn:aws:kms:${region}:${accountid}:alias/${alias}" > ~/.sops.yaml
# Verify the configuration
cat ~/.sops.yaml
Once this is executed, it returns the configuration of your sops.yaml file to ensure that it is correct, as shown in the image below.
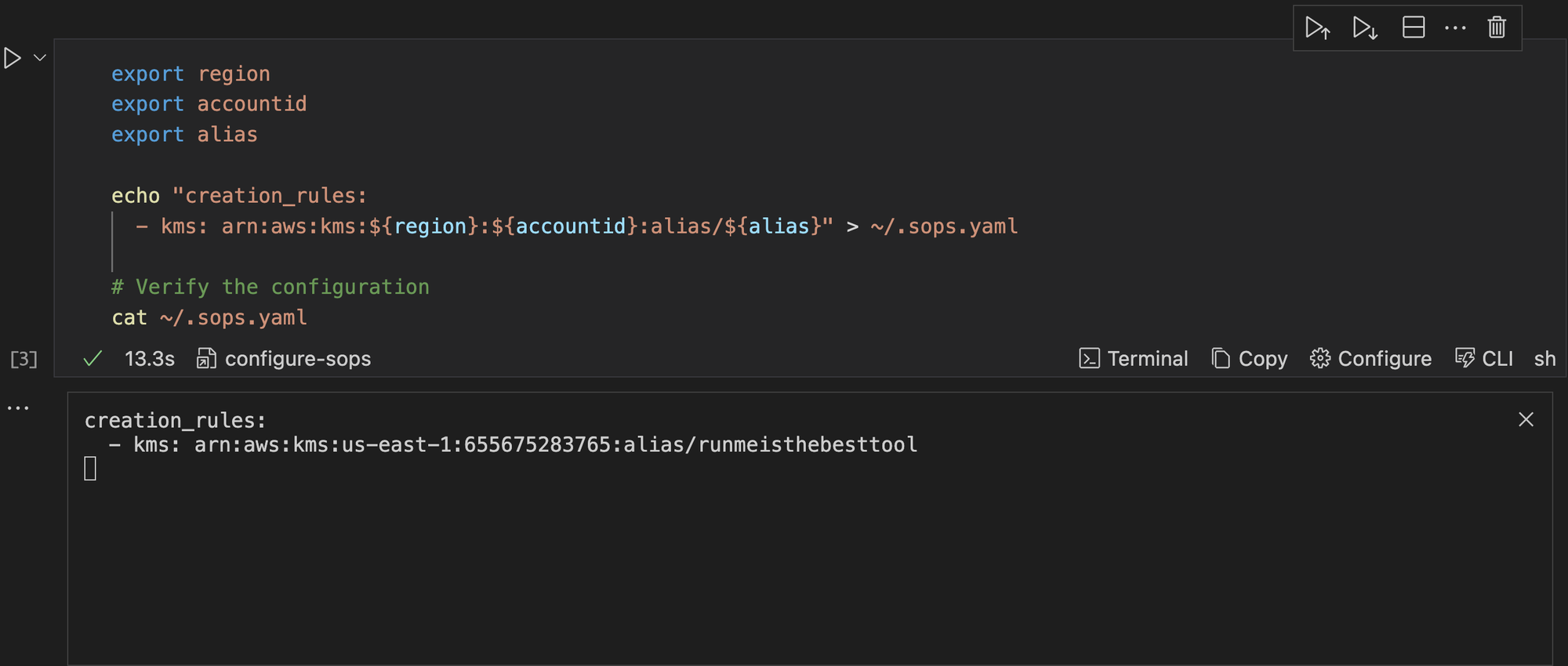
Encrypt Your Secrets
To encrypt your secret using SOPS with AWS KMS, ensure you have set the following:
- Your environment variables.
- Your manifest
runme-secrets.yamlfile containing your secrets. If you have not done this, create one using the following YAML manifest in our repository . - Click the execute cell button.
keyid=$(aws kms create-key --description "runme-key312" | jq -r '.KeyMetadata.KeyId')
sops --encrypt --kms arn:aws:kms:${region}:${accountid}:key/$keyid --encryption-context Role:runme-test --encrypted-regex password runme-secrets.yaml > runme-secrets-enc.yaml
Now, we have successfully encrypted your secrets within runme-secrets.yaml. Runme automatically transfers your information to run me-secrets-enc.yaml.
Decrypt Your Secrets within the Runme cell
Similar to the encryption process, Runme you can decrypt your encrypted security in your Markdown file. This will ensure that every process is properly automated. You can do this in two ways.
- To check for your secret within the cluster, run the command below:
kubectl get secret runme -n test -o jsonpath="{.data.password}" | base64 --decode
- To decrypt your SOPS secret, run the command below:
sops --decrypt --kms arn:aws:kms:${region}:${accountid}:key/${keyid} --encryption-context Role:runme-test --encrypted-regex password runme-secrets-enc.yaml > runme-secrets.yaml
Here is a pictorial representation on what happens when you decrypt your secrets within your Runme cell.
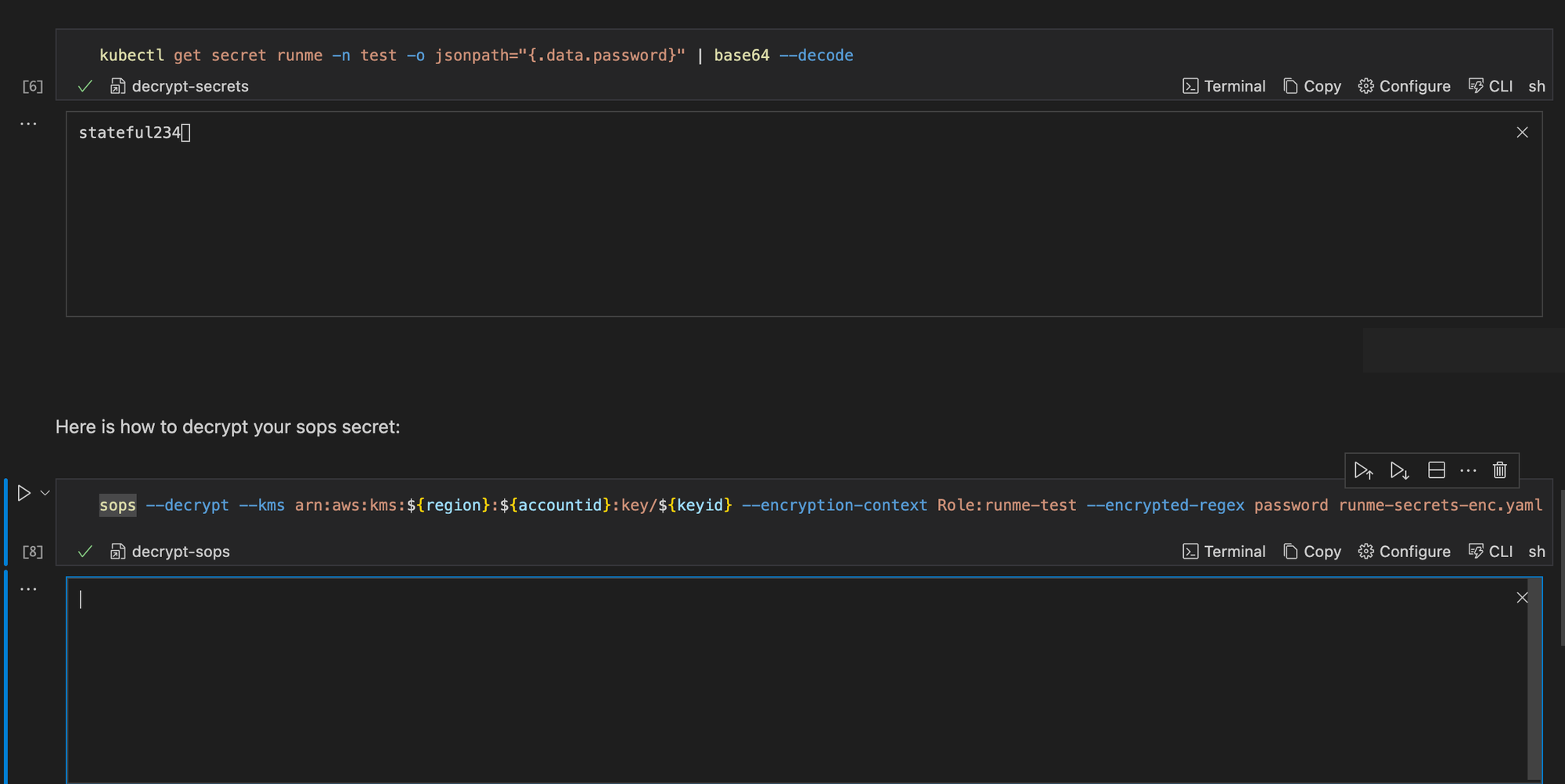
When you decrypt the secret, it moves the decrypted secrets from a SOPS-encrypted secret runtime-secrets-enc.yaml into the original version before it was encrypted runme-secrets.yaml
Apply Encrypted Secret
To apply the encrypted secrets in your runme-secrets-enc.yaml file, run the command below.
sops -d runme-secrets-enc.yaml | kubectl apply -f -
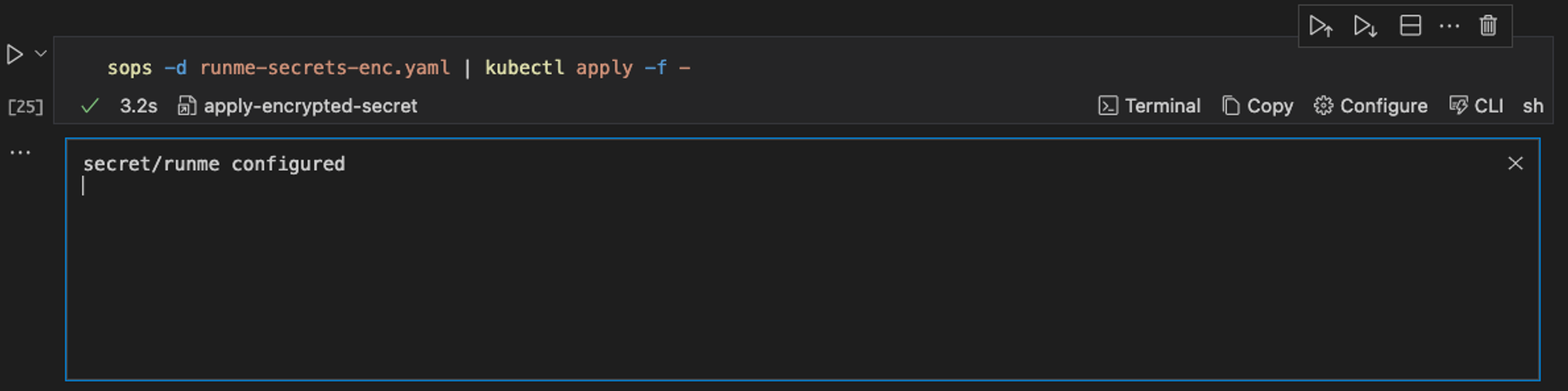
This runs the runme-secrets-enc.yaml file decrypts it and then applies the file.
Improved Documentation Experience with Runme Notebook
We successfully encrypted our Kubernetes secrets inside our Markdown file. Runme makes your automation process easy with its features.
One of the useful features within the notebook environment is the environment variable prompt feature, which allows users to input values directly within the notebook environment and use them whenever needed rather than inputting them again.
Another amazing key feature of Runme is the Autosave feature, which automatically records and tracks every change and activity in your processes without manual intervention.
Visit the Runme Documentation to learn more about Runme and explore its features. Then, begin your journey to automating your operations processes.